Usage Logger 2 - Walkthrough
Contents
Introduction
Usage Logger 2 is an Android app that records or extracts data about how a person uses their smartphone. Primarily developed to assist with psychological research and behavioural science more generally, the app can be customised to perform a number of different functions. This includes the ability to extract historical data about previous (retrospective) usage from the previous 1-5 days.
Publications
Geyer, K., Ellis, D. A., Shaw, H., Davidson, B. I., & Keil, T. F. (2023, March 7). Open source smartphone app and tools for measuring, quantifying, and visualizing technology use. PsyArXiv. doi: 10.31234/osf.io/eqhfa
Geyer, K., Ellis, D.A., Shaw, H. and Davidson, B. I. (2022) Open-source smartphone app and tools for measuring, quantifying, and visualizing technology use. Behavior Research Methods, 54(1), 1-12. doi: 10.3758/s13428-021-01585-7
Other resources
- Android App on Google Play Store.
- Customise what data the app collects.
- Decrypt collected data.
- Sample data and scripts for analysis.
- Privacy Policy
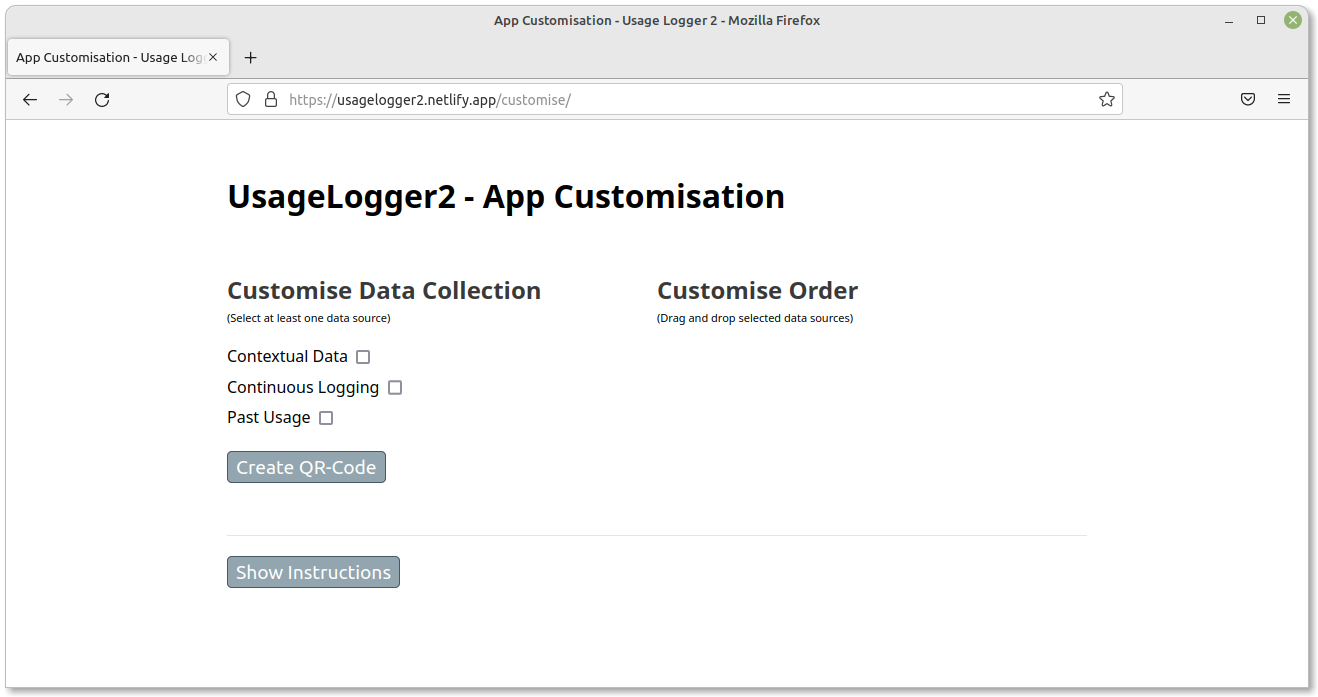
Customisation
The customisation website allows the researcher to choose how the app will function. There are three different data streams that may be employed and altered. Additionally, the researcher can customise the order that the data sources are queried.
Specify the type of data to collect:
1) Contextual Data
Contextual data provides a researcher with a snapshot of what software is installed on the smartphone. Data captured can include:
- Apps installed: What apps are installed on the device?
- Permissions requested: What permissions have been requested by which apps? Permissions provide access to particular restricted data like phone call logs or location. See here for more information.
- Response to permission request: Has the user provided the permission or not?
2) Continuous Logging
Continuous logging records smartphone interactions after installation of the app. These can include:
- Screen usage: Record when the screen was on/off.
- App usage: Record at what point apps were used and store the identity of the apps.
- Notifications: Record which apps sent notifications.
- Changes in installed apps: Record if any apps were installed/uninstalled.
- Phone usage: Record when the phone was on/off (default setting, not customisable).
3) Past Usage
This will provide information about the phone was used for during the last few days (max. 5 days ago).
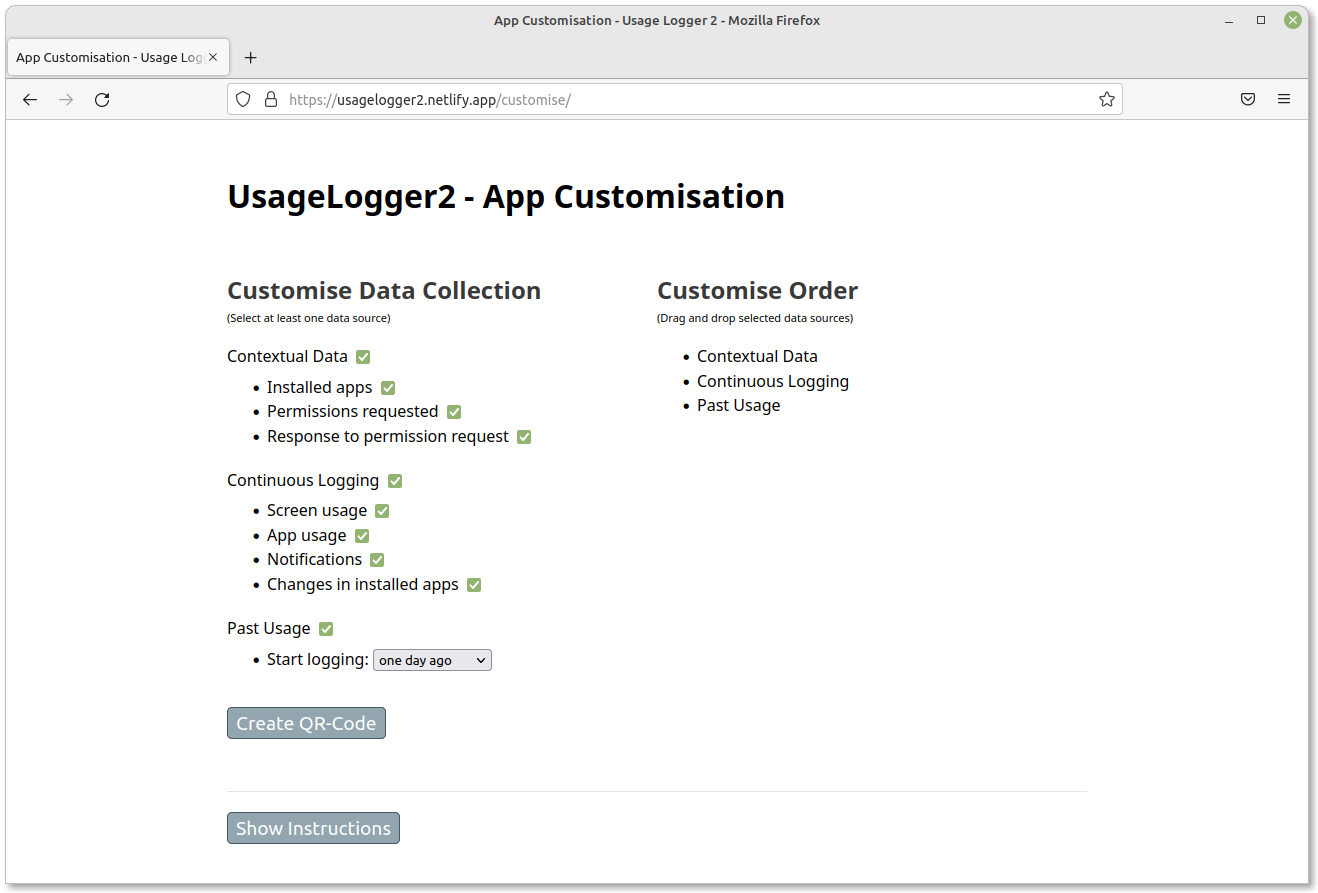
Customise Order
Customise the order in which the data is collected by dragging and dropping the text on the right hand of the screen that appears after you have demonstrated that you want a piece of data collected.
If you have checked all the options on the website, it may look something like this.
Create QR-Code
Clicking the 'Create QR-Code' button will generate a QR-Code image. This is required to customise the app. Users must scan the QR-Code from within the app, which will then start the data collection process. The QR-Code can also be downloaded, which is helpful if you want to reuse the same configuration settings in the future.
Android App
The app can be found on Google Play Store:

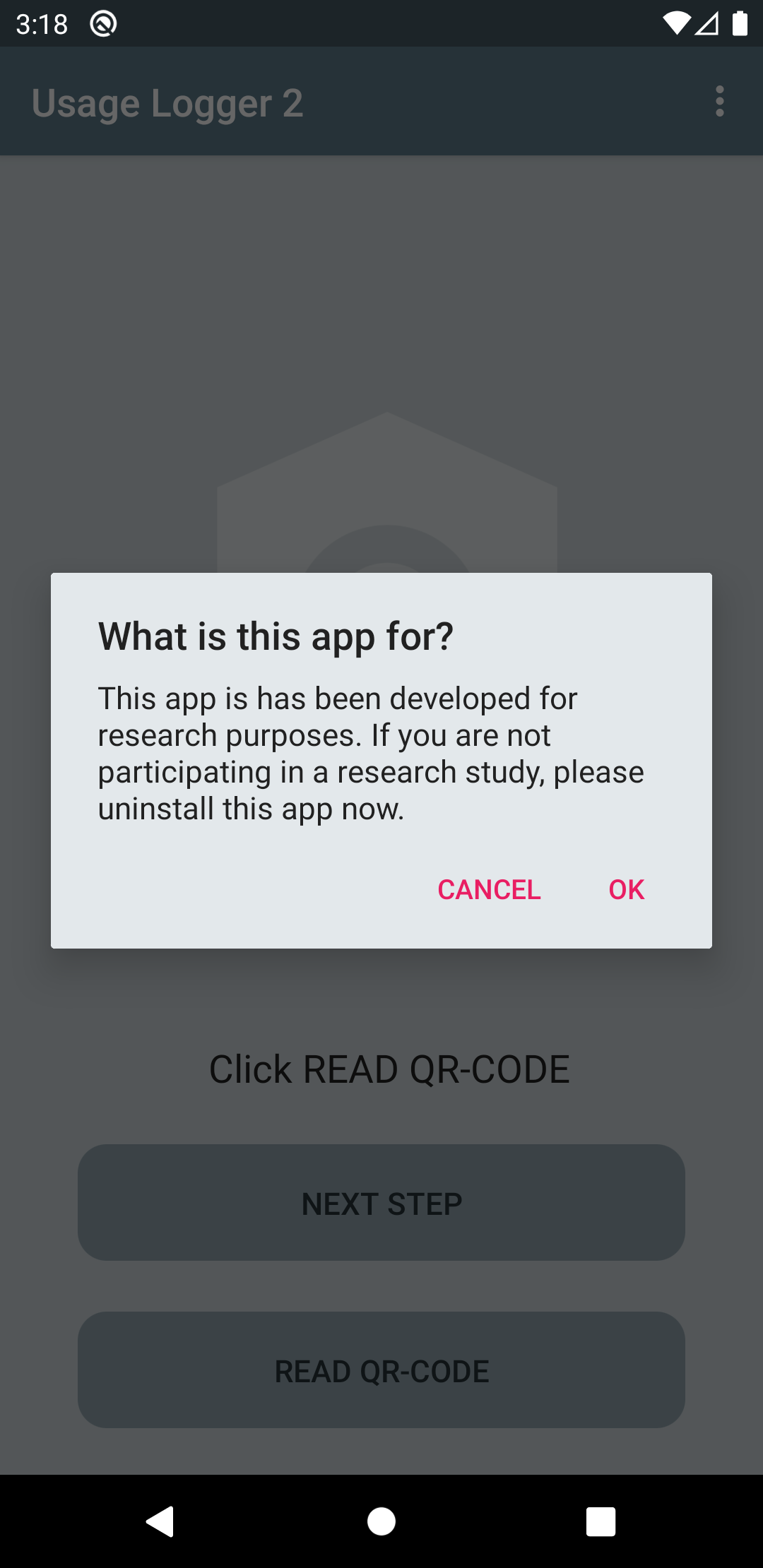
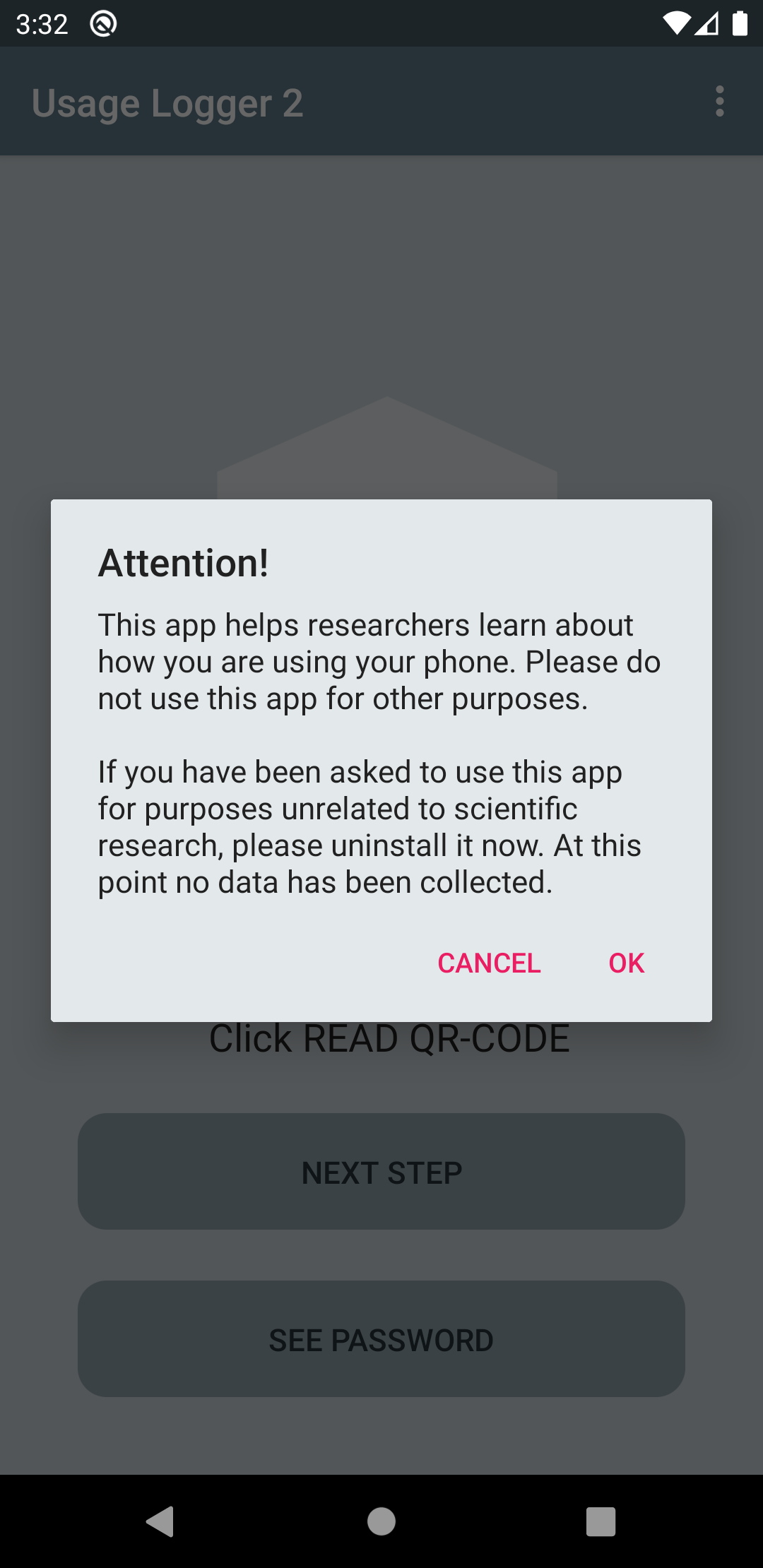
Users can install the app by visiting the google play store listing. When opening the app it will first display a message informing the user that the app is only intended for scientific research.
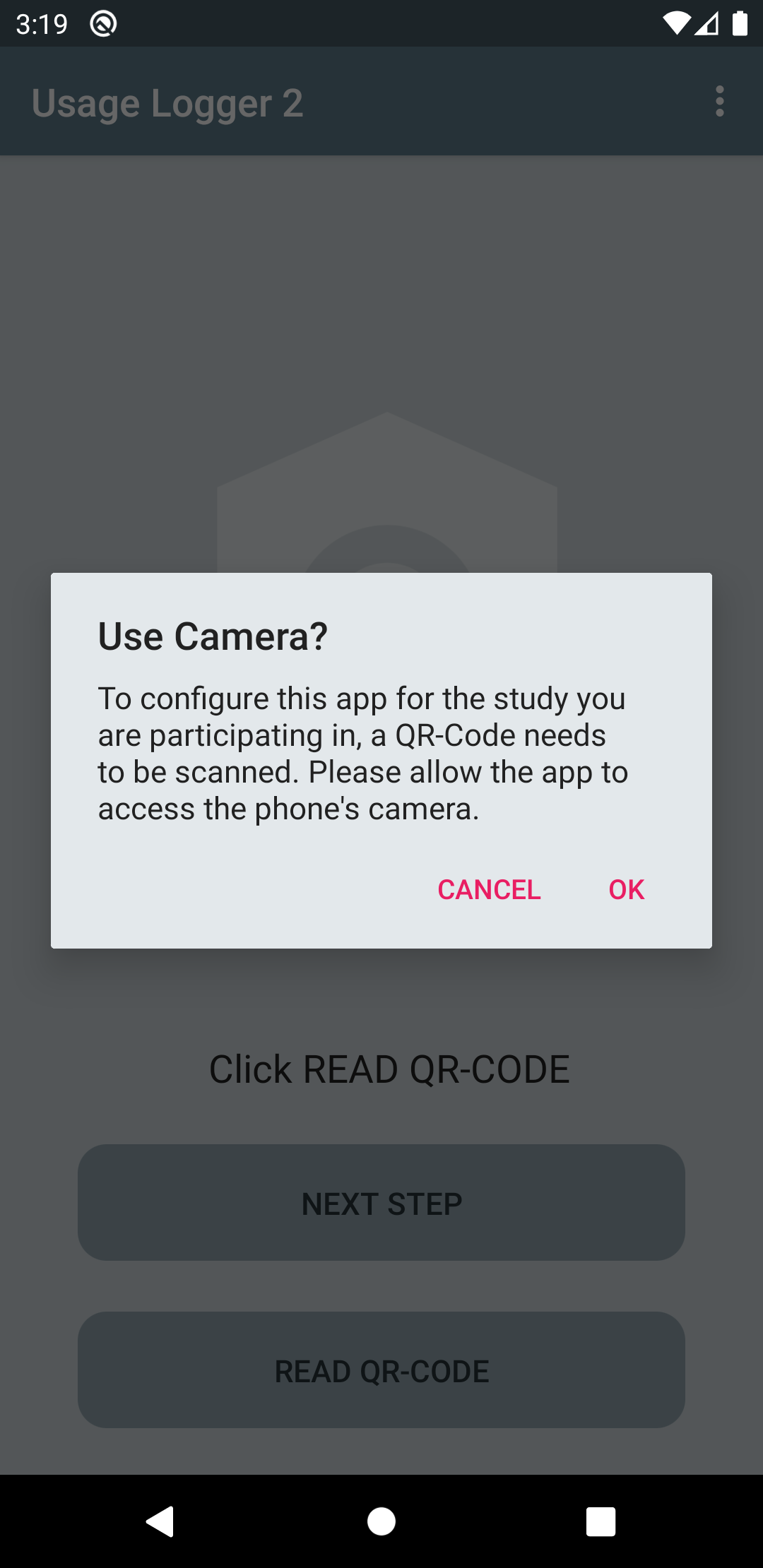
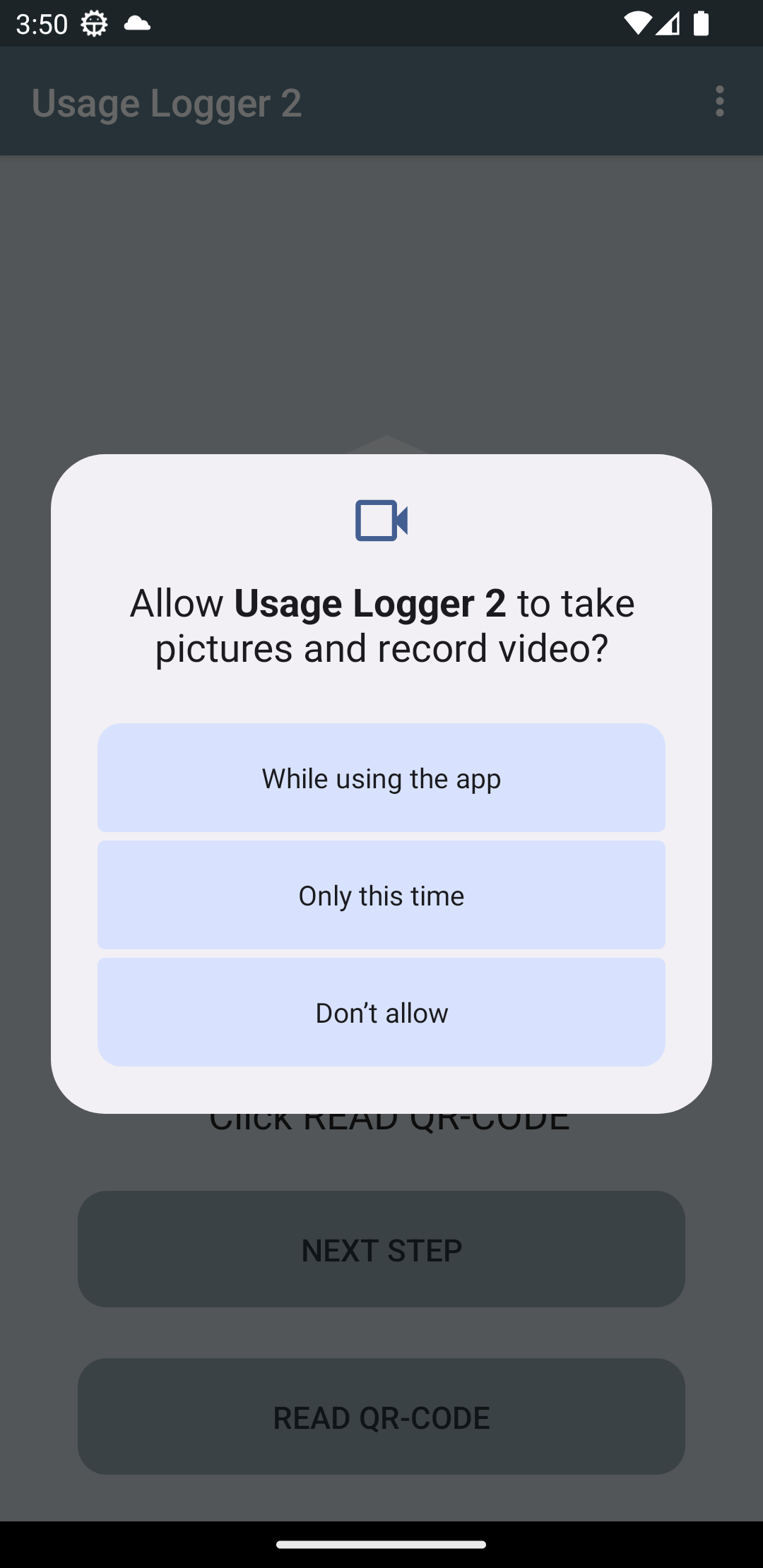
The user is then informed that the app would like to use the device's built-in camera. For this, permission to access the device's camera is required. This permission is essential in order to scan the QR-Code.
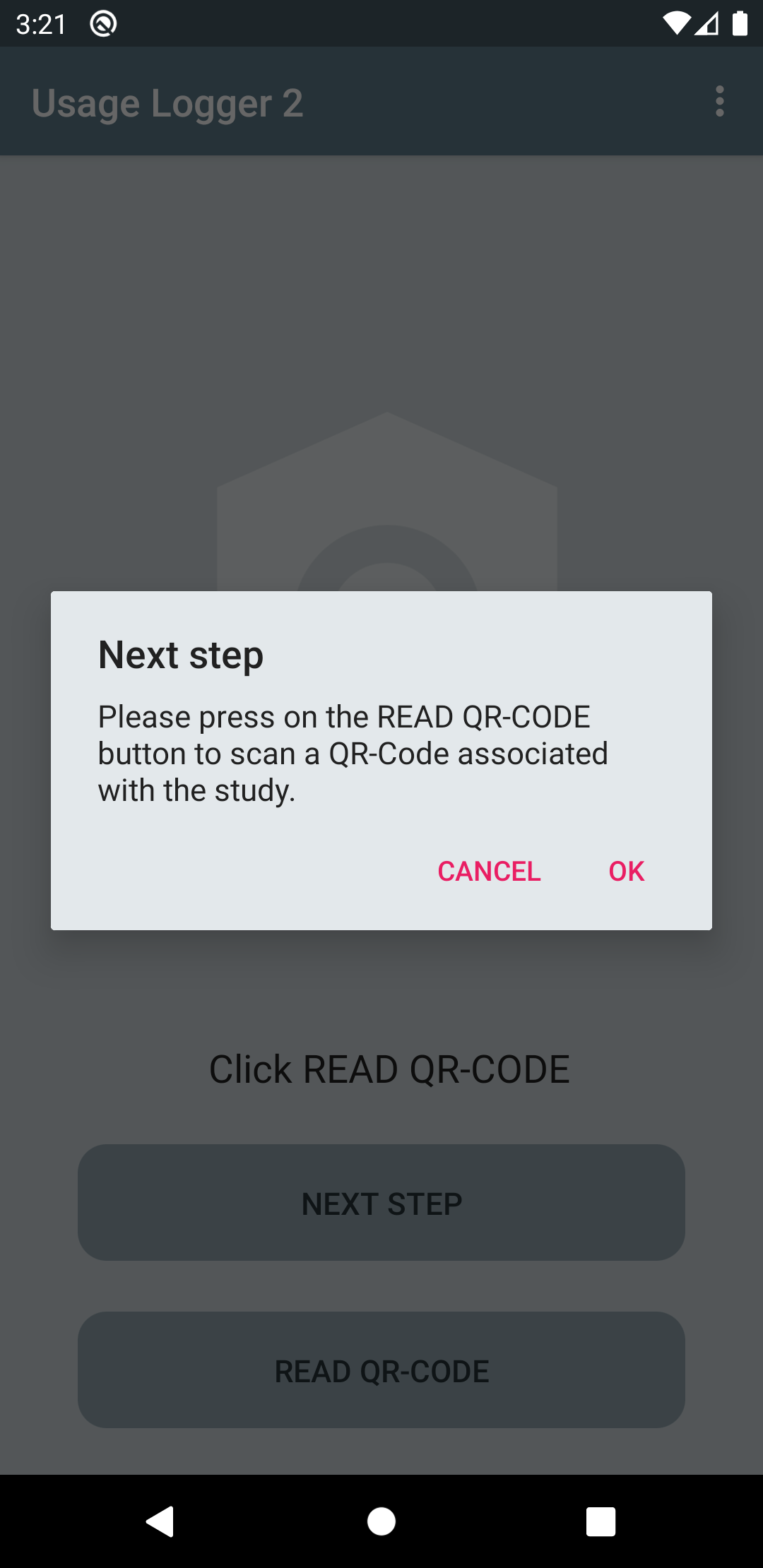
Users will then be asked to press the "READ QR-CODE" button to scan the QR-Code provided by the researcher (produced by the customisation website; see above).
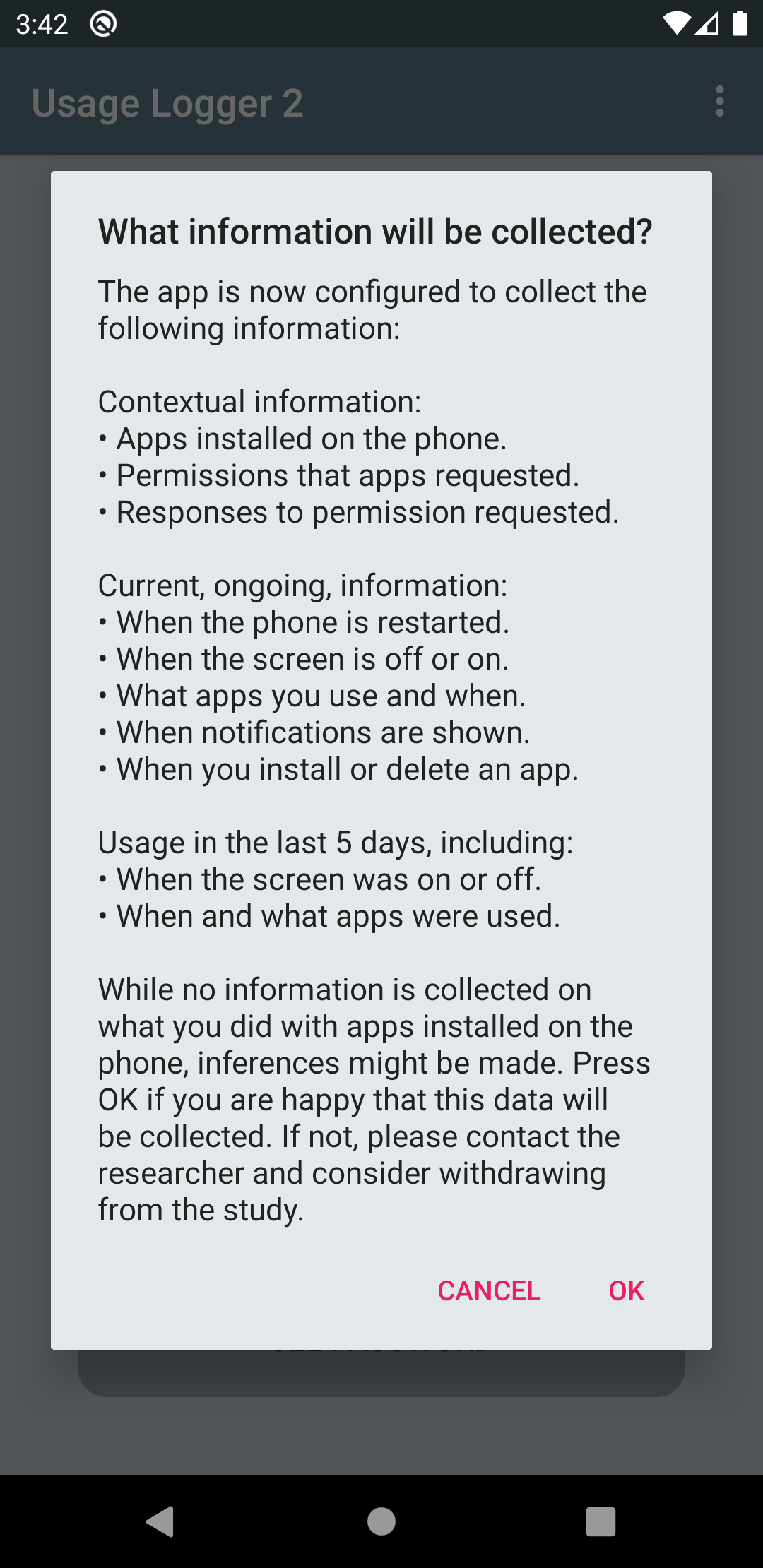
After the QR-Code is scanned, the user will again be informed that data collection is only intended for scientific research. They will also be informed about what data is going to be collected by the app (which depends on how the QR-Code was previously configured). The image below shows a message that would be displayed for a configuration that collects all three data types.
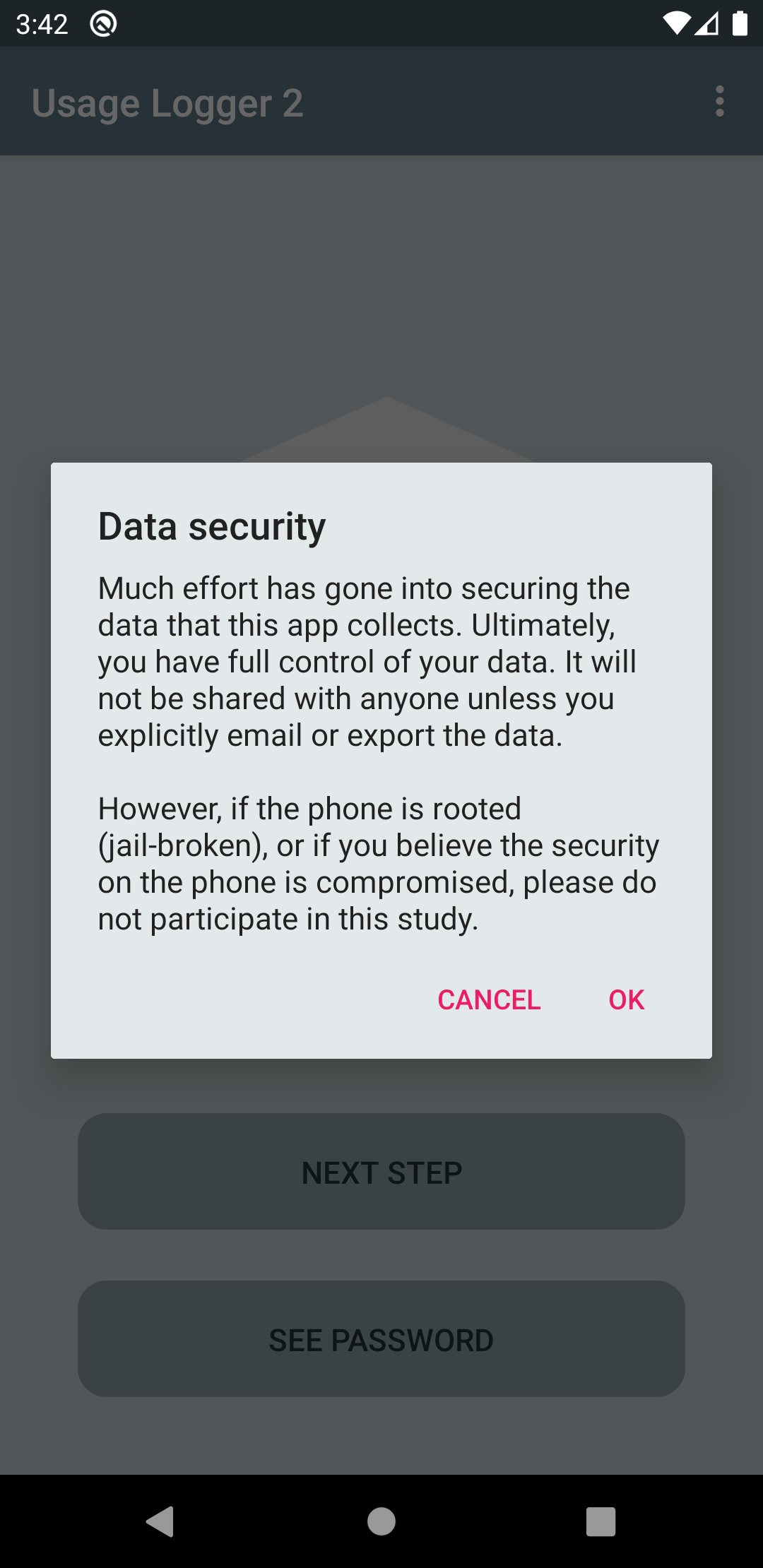
Data Security and Permissions
Next, the user will be informed about data security. For a detailed guide of the security features implemented by the app, please consult the preprint and/or publication.
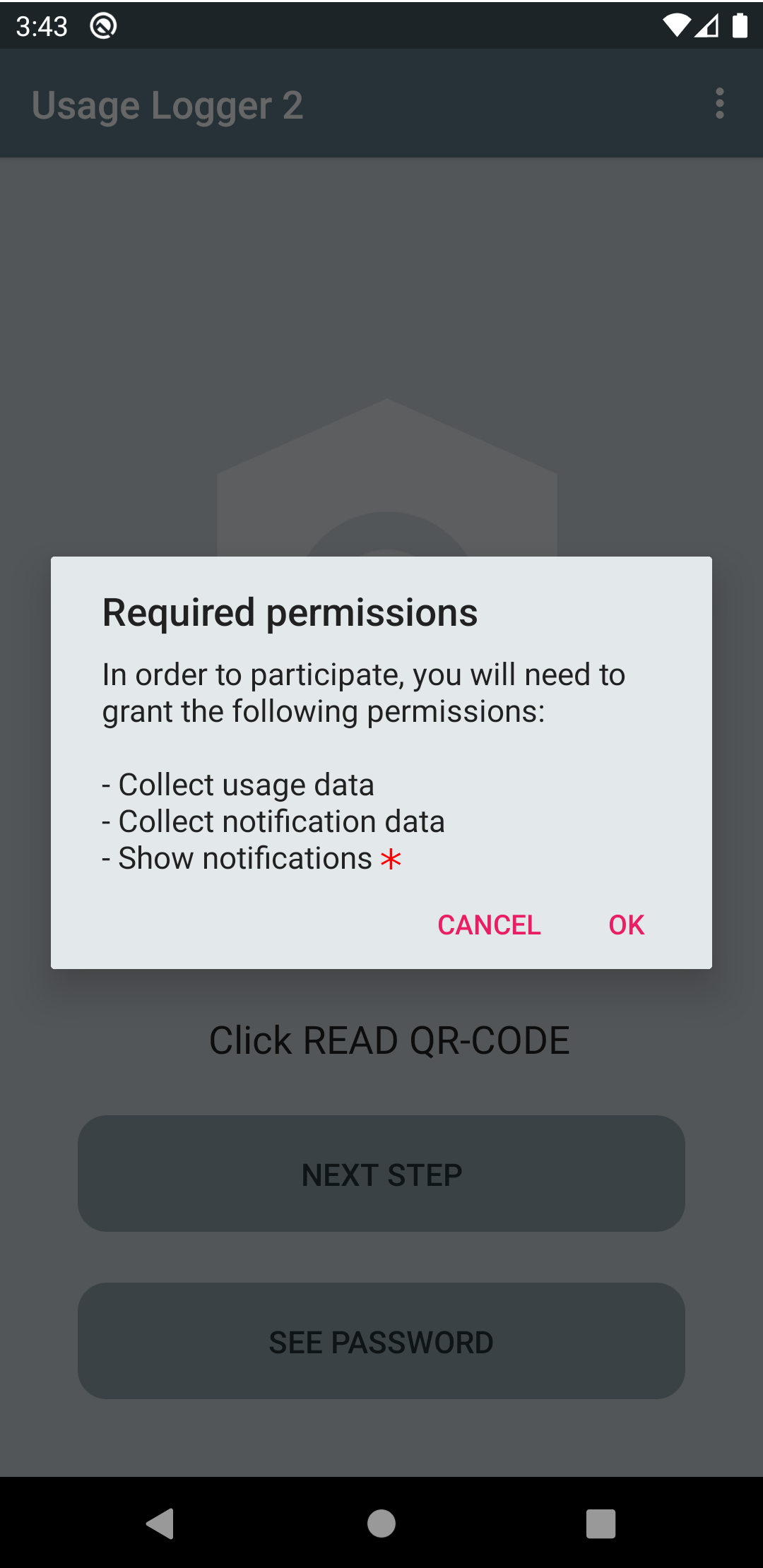
Then, information about which permissions are required to carry out the data collection is shown. This may include the collection of usage and notification data and permission to show notifications (* "show notification" permissions are only requested from Android 13 and above).
The user is forwarded to the settings that allow them to permit the required permissions. The look and feel of the permission settings may vary slightly depending on the Android version installed.
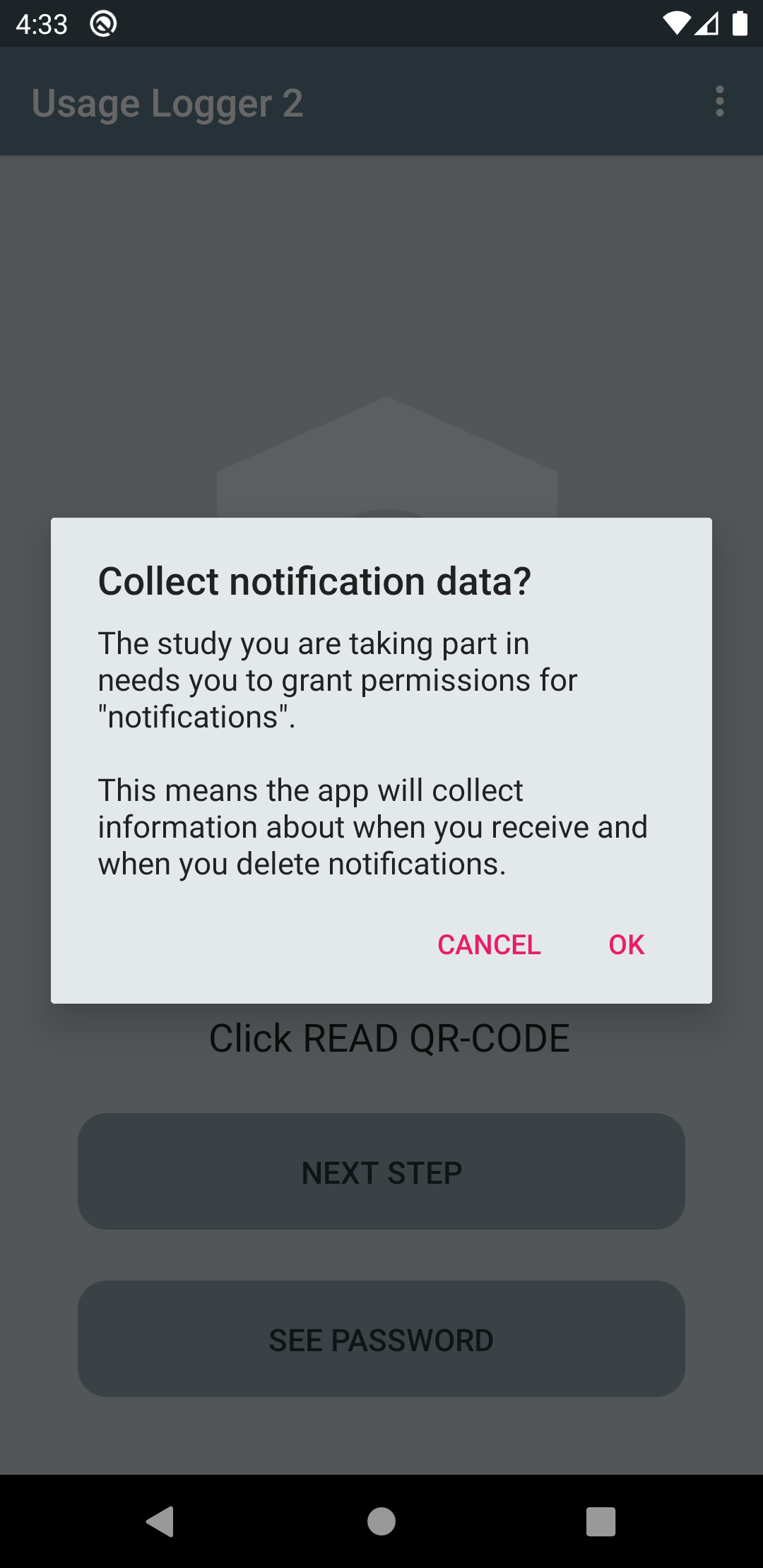
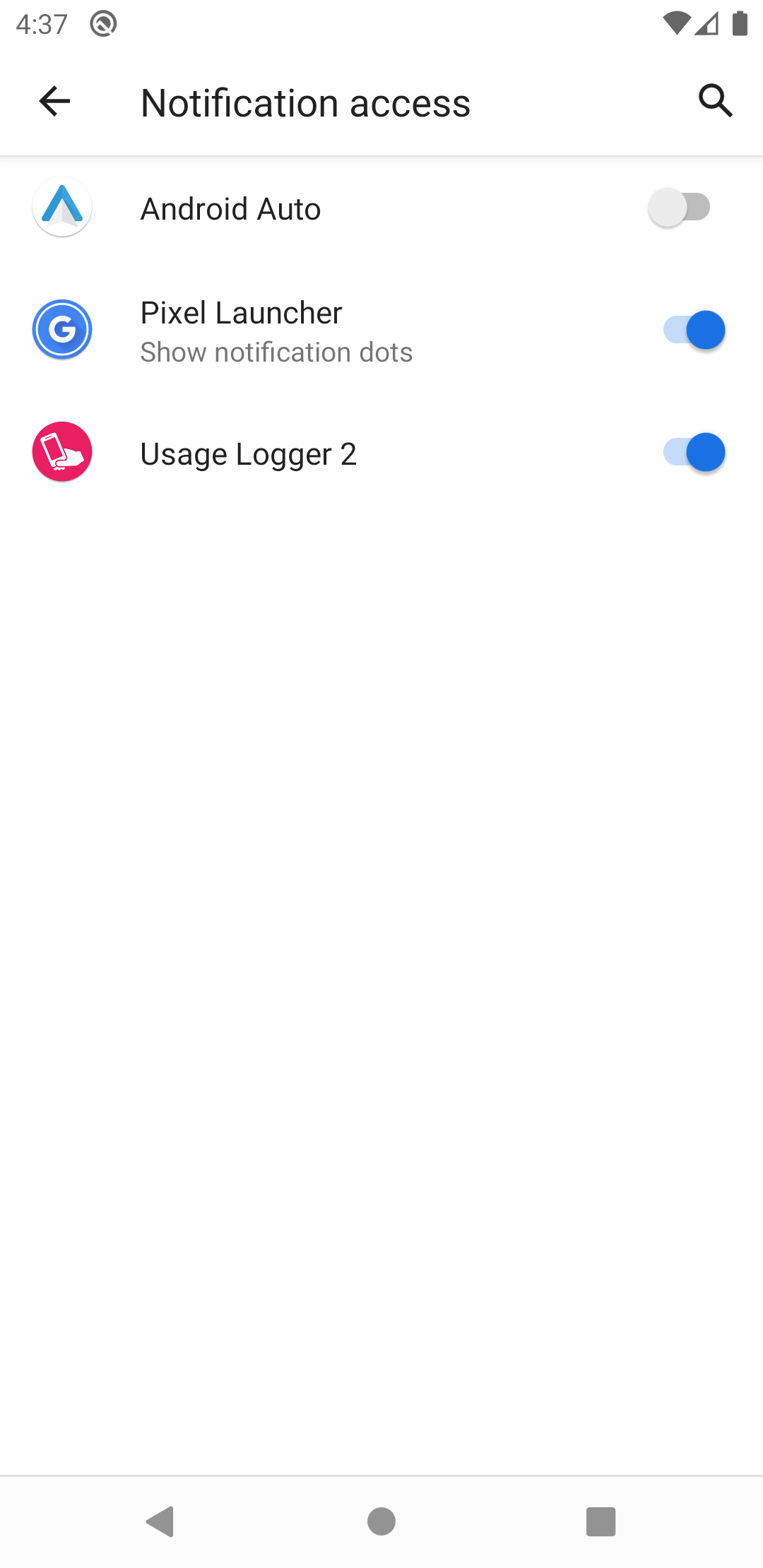
Notification permission
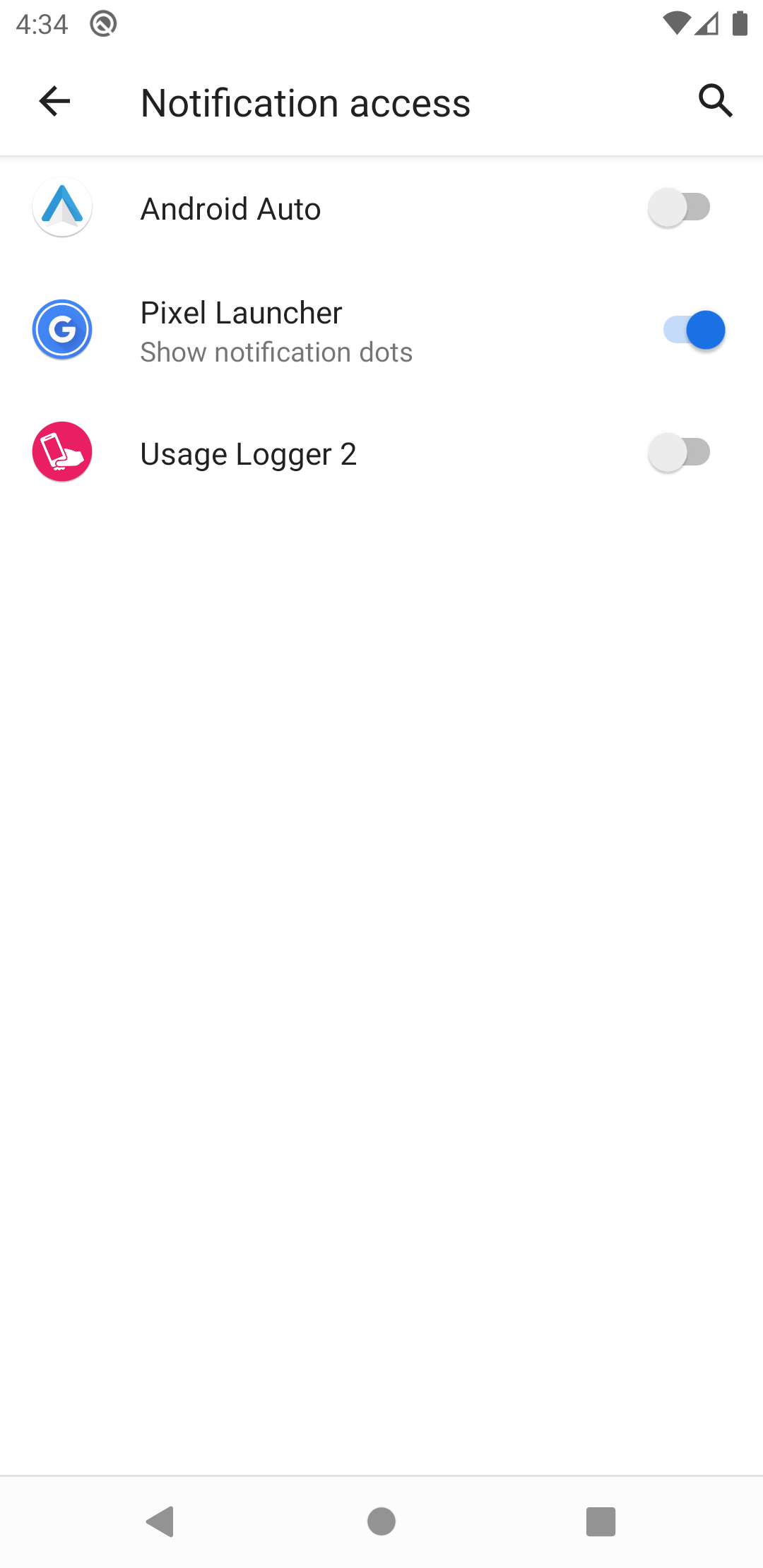
For the notification permission, the user will is informed of what this involves. They will then have to select enable "notification access" for the Usage Logger app.
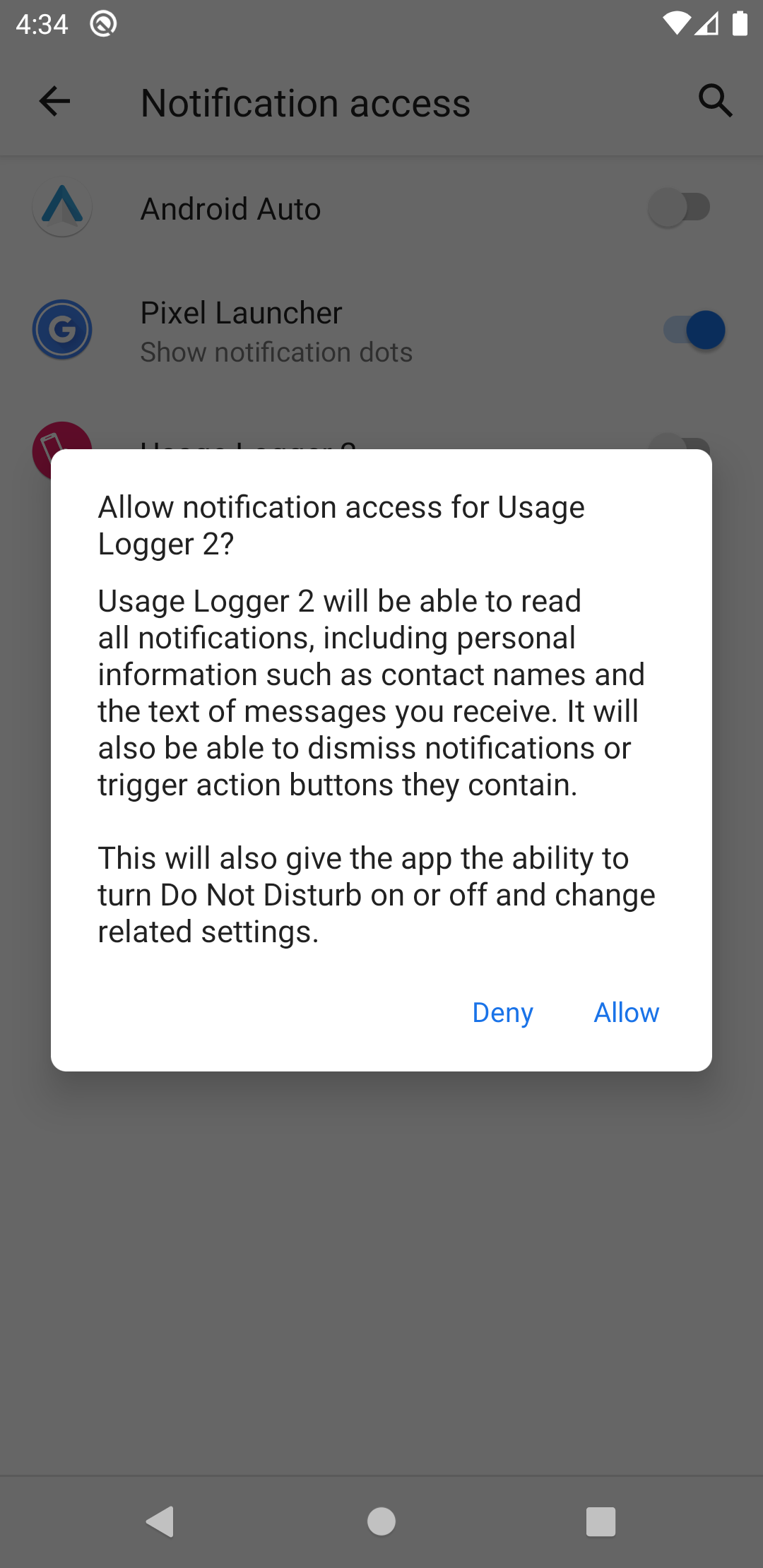
On enabling "notification access" for the Usage Logger app, a warning message may appear informing the user of all potential security problems that emerge as a result. While this permission provides wide-ranging capabilities, this app only records when and which app is providing notifications. Here, the user will have to confirm the permission request by selecting "Allow".
After the user enables this permission, they need to return to the app. This can be achieved by pressing the back arrow at the bottom of the screen (depending on the Android OS, in some cases the back button may be at the top of the screen). Important: The user should not exit the app to the home screen, as this may interfere with the running of the app. Instead, they should just press back after having accepted this permission.
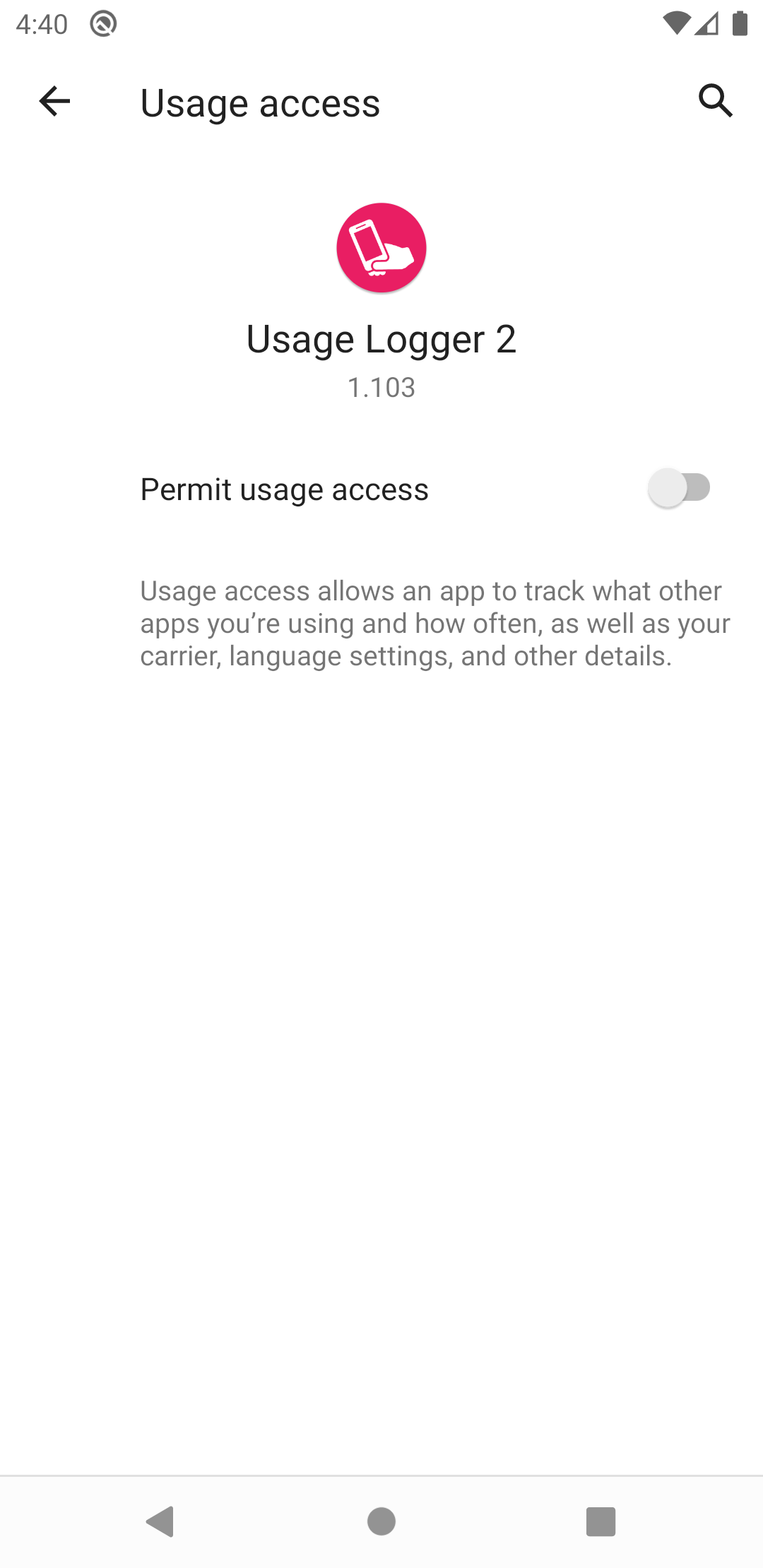
Usage permission
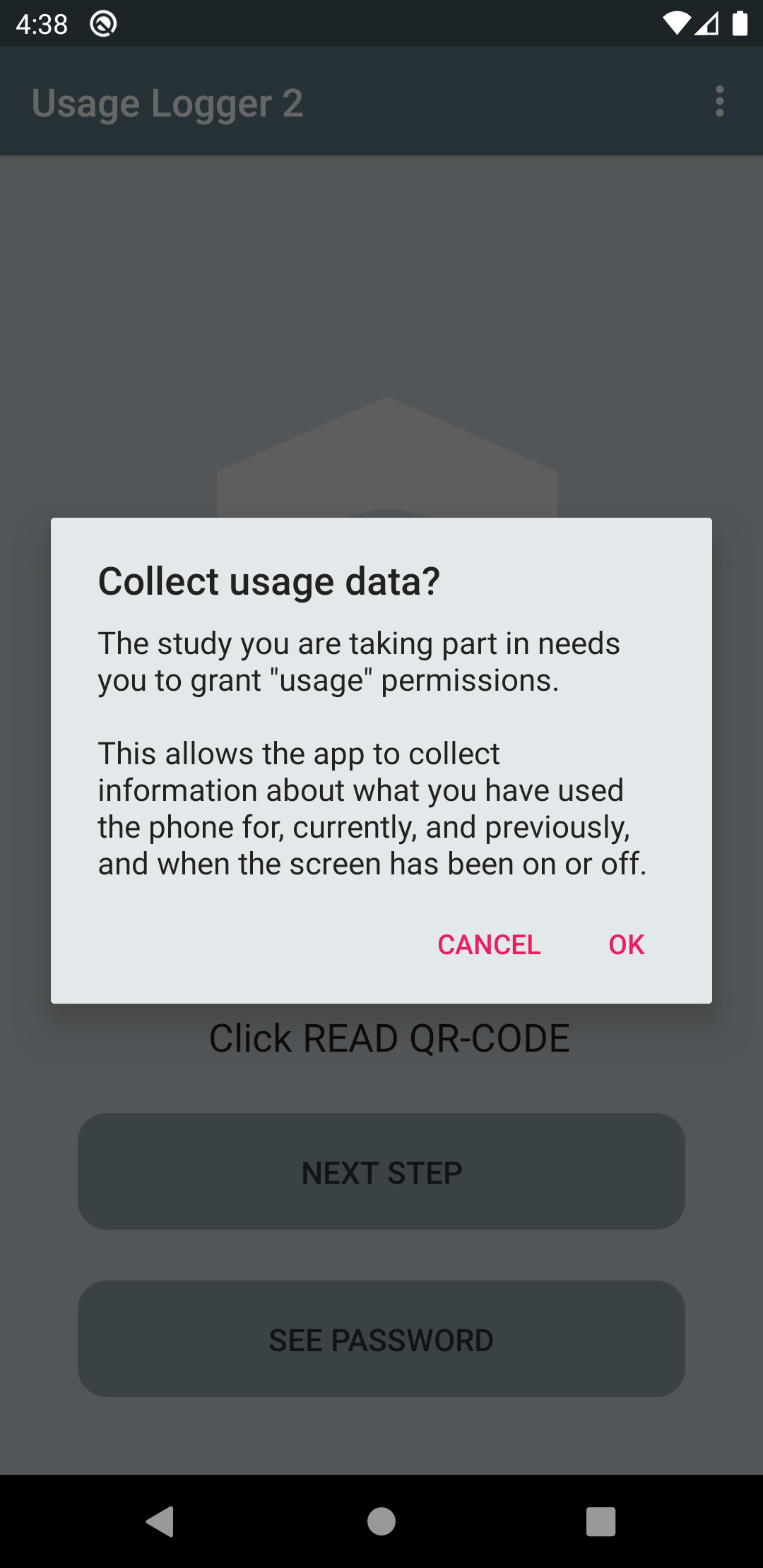
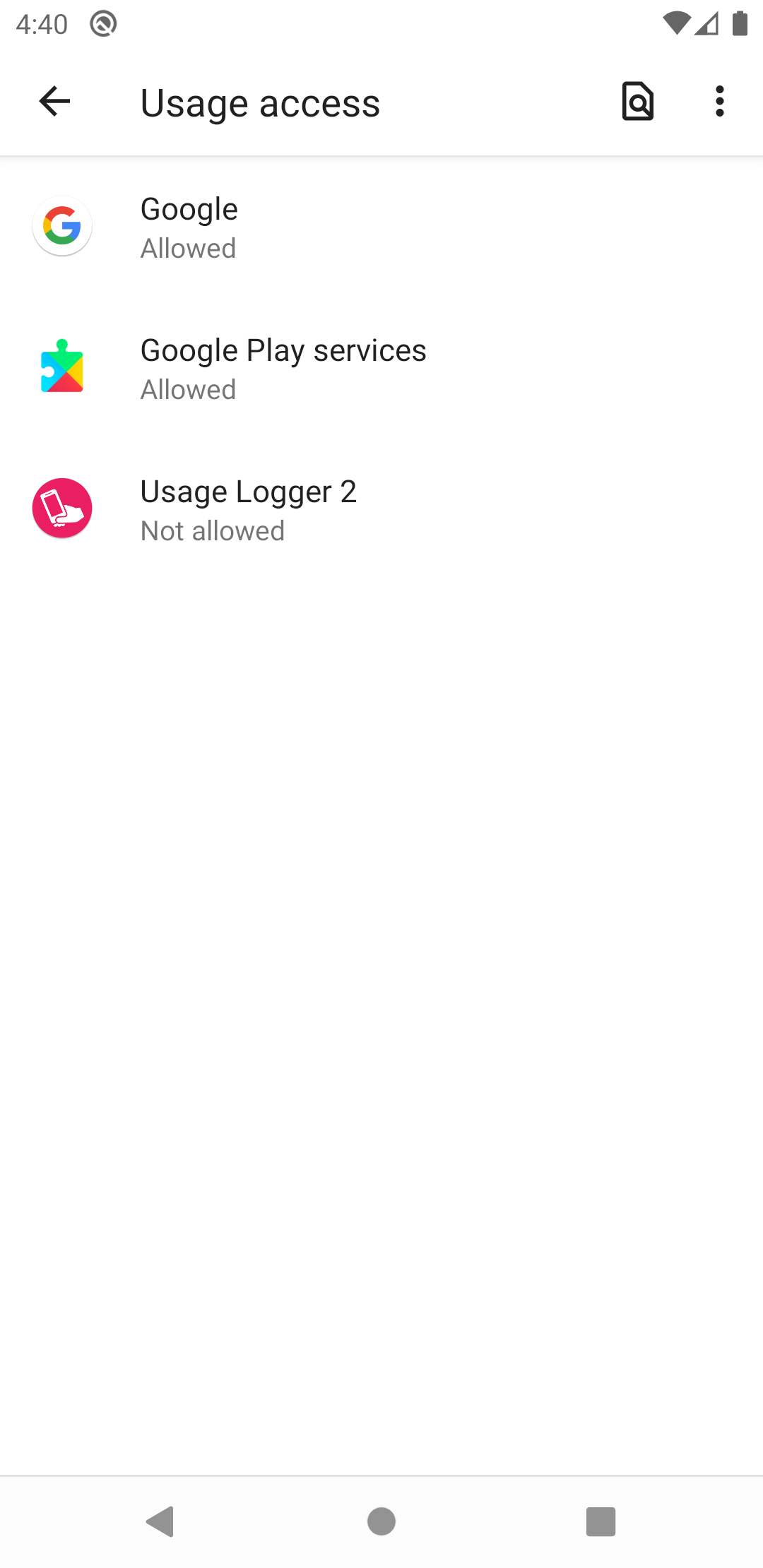
Upon returning to the app, the user may be requested to allow usage access. If usage permission is not requested, then the app will simply start working (as described below). Similar to the notification permission, the users will initially be shown a message about what permission is required and what it is used for. After confirming the message, the user must select the Usage Logger listing in order to grant usage permission for this app.
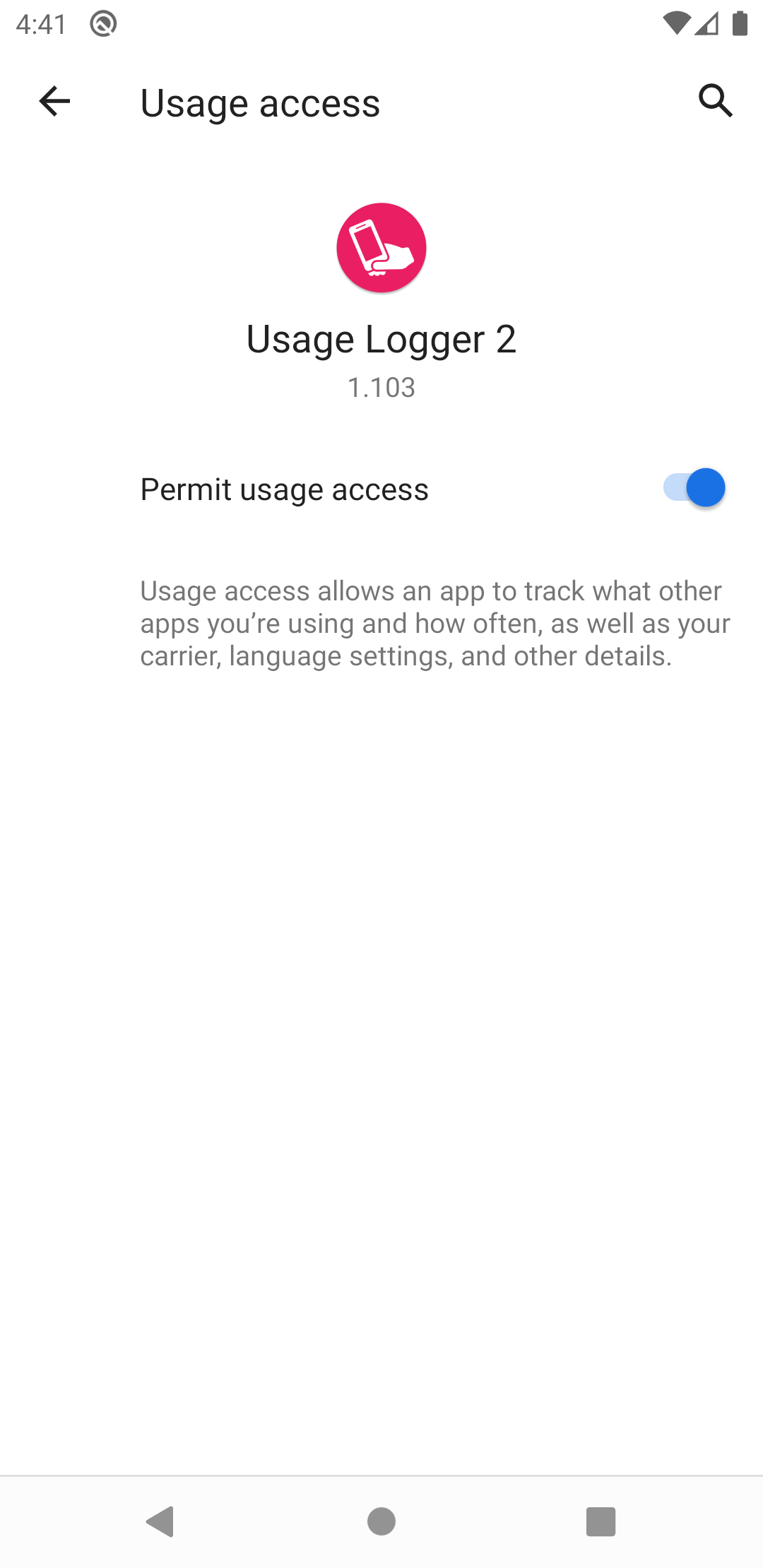
Then the user will need to enable "Permit usage access" and return to the app as before. This can be achieved by pressing the back arrow twice at the bottom of the screen (depending on the Android OS, in some cases, the back button may be at the top of the screen).
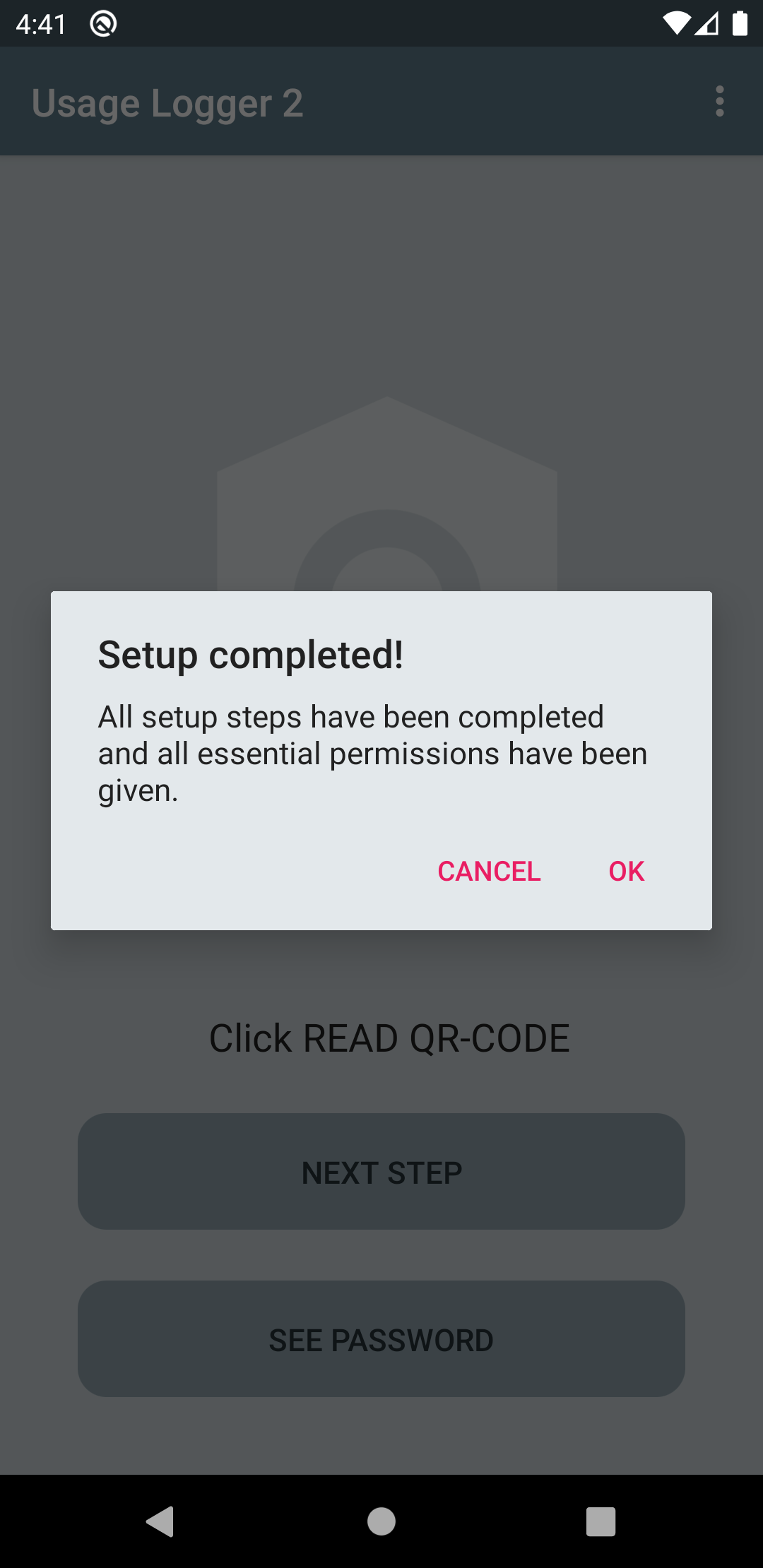
Upon returning to the app, the user should now see a confirmation message informing them that the setup is now complete.
Running of the app
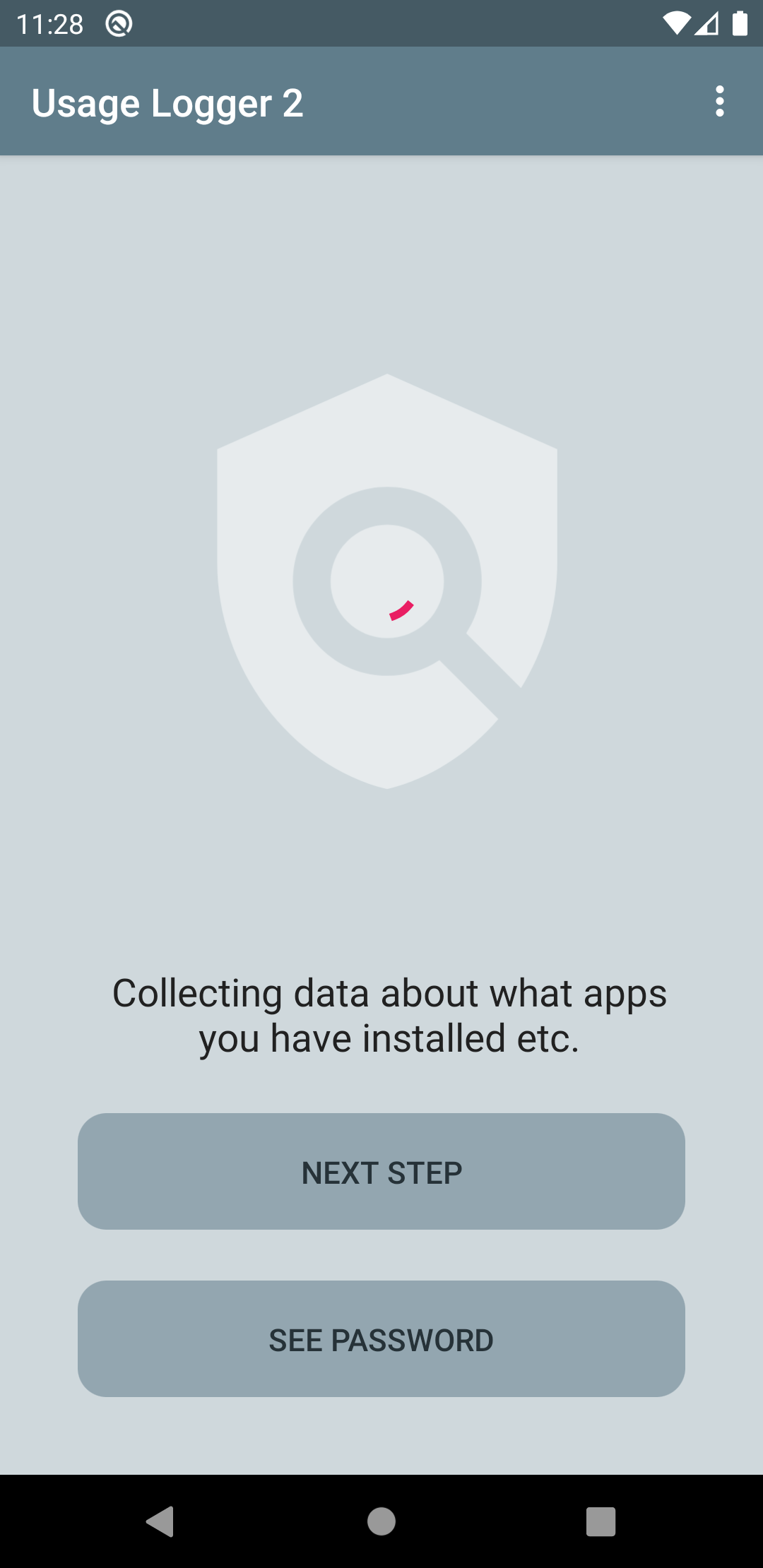
Depending on how the app was customised (see above), the app may collect contextual and past usage data and continiously monitor and log current use. As a result, the app quickly scans the phone to collect contextual and past usage data. Therefore, messages to show which data is being collected may only be shown very briefly.
The app will continue to show that it is currently collecting data, if continuous logging is configured. This data is collected in the background, even if the user closes the app. The user is informed of this through a notification in the status bar.
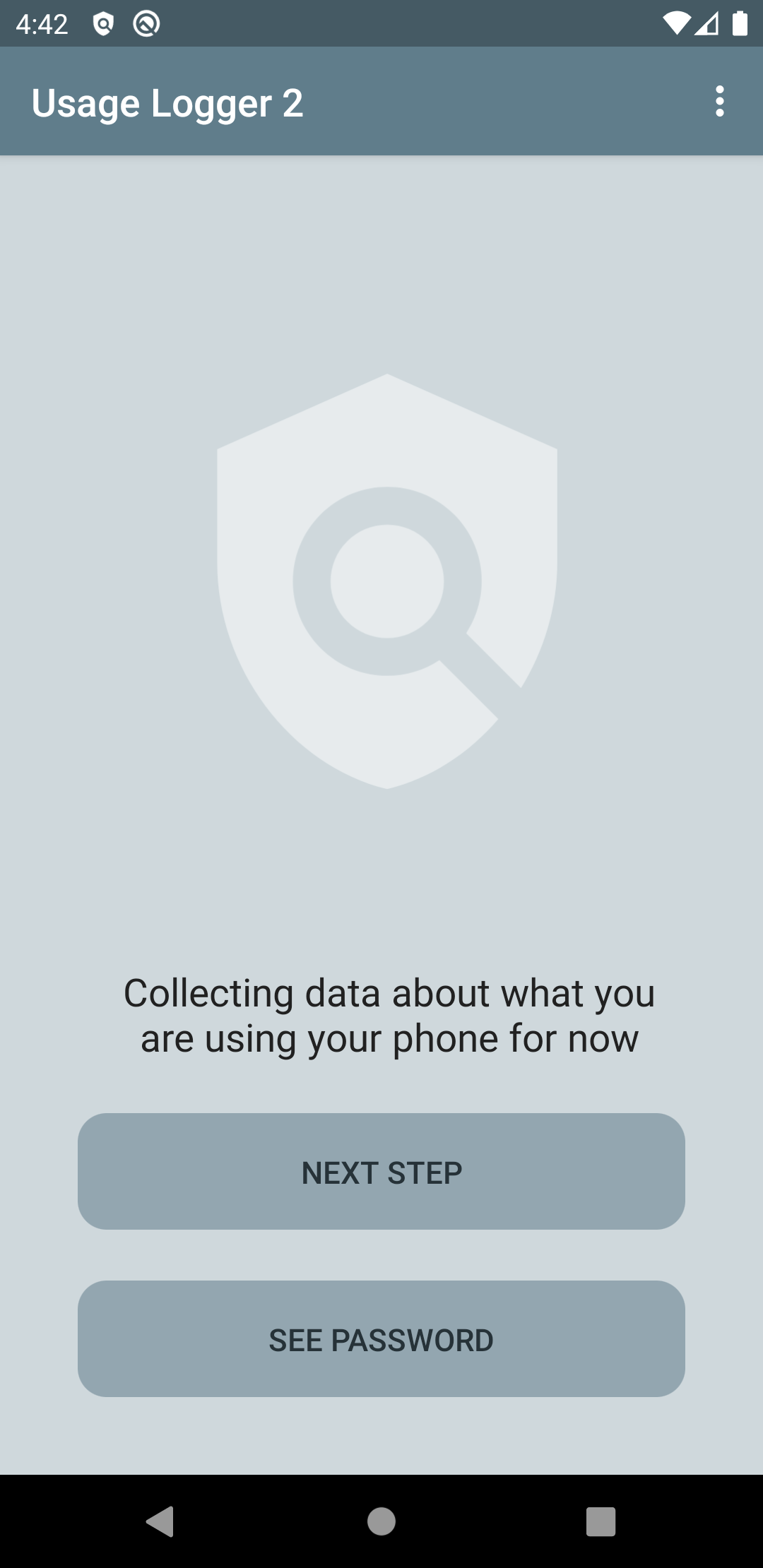
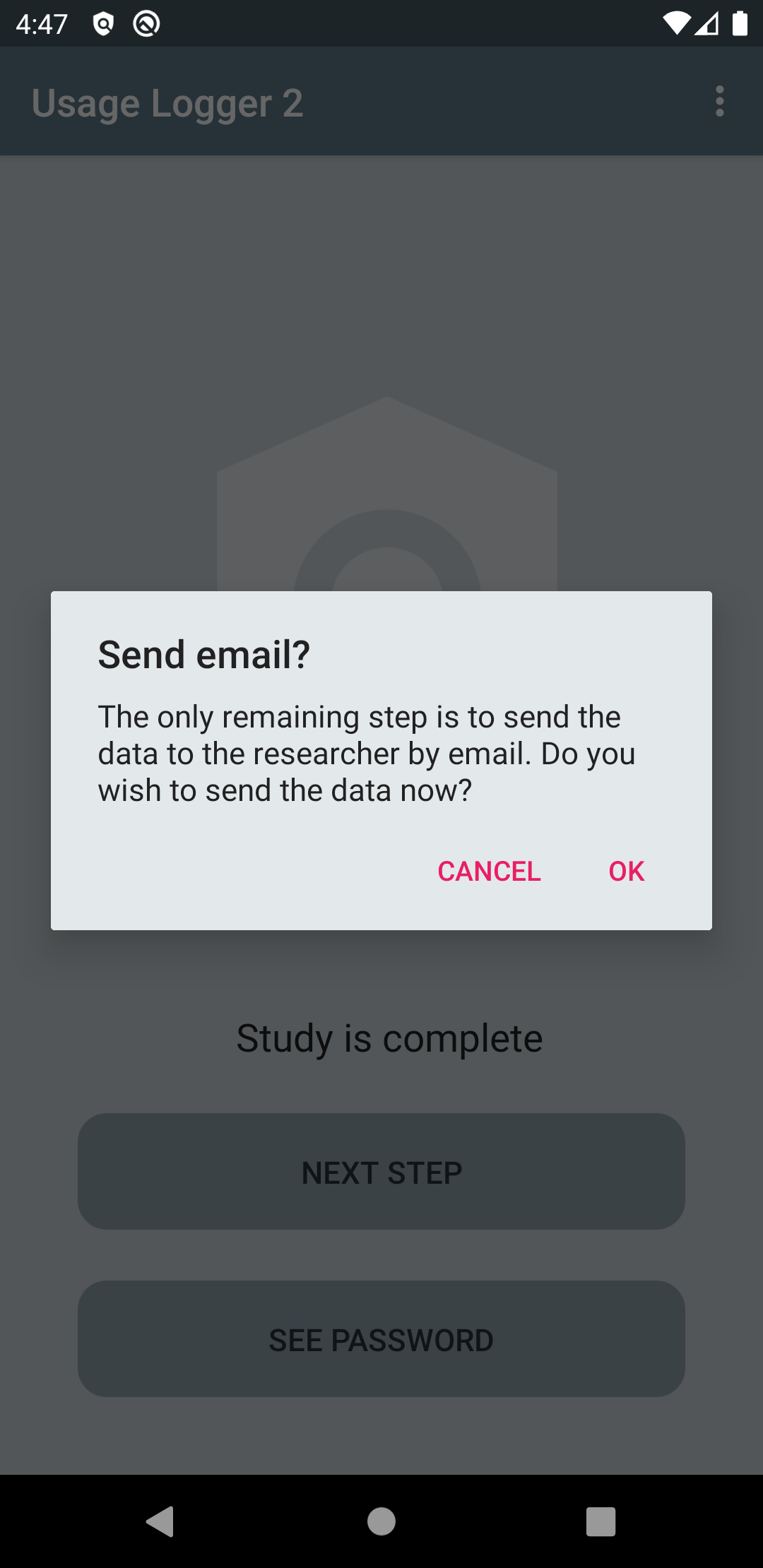
When the user presses "NEXT STEP," logging stops, and the rest of the data is collected. A popup will then ask the user to confirm that they wish to end data collection and send the data to the researcher. Upon confirmation, they will be asked to select an appropriate app (which apps are shown depends on which apps are installed on the device) to send the encrypted data files (PDFs) to the researcher.
After sending the data, the user needs to communicate the password to the researcher in order for them to be able to decrypt the data. The password is shown to the user by pressing the button "SEE PASSWORD." The password should not be sent via Email or any other platform that was also used to send the data. Qualtrics or some other secure platform can be used to record this information.
Decryption and Conversion
The decrypt and convert webpage can be found here.
At this point, the data has been collected and sent to the researcher. However, it still needs to be decrypted and converted to a suitable file format. While you can open the file by entering the password, the table format of the data is not easy to analyse. It is best converted to a CSV or other format. Various R and python packages can be used, but most packages don't seem to function well with the Usage Logger output. This is because these packages typically do not support two-column or multi-line data. Therefore, if a long app name requires two lines, half the text may be listed on a new line and may thus be counted twice.
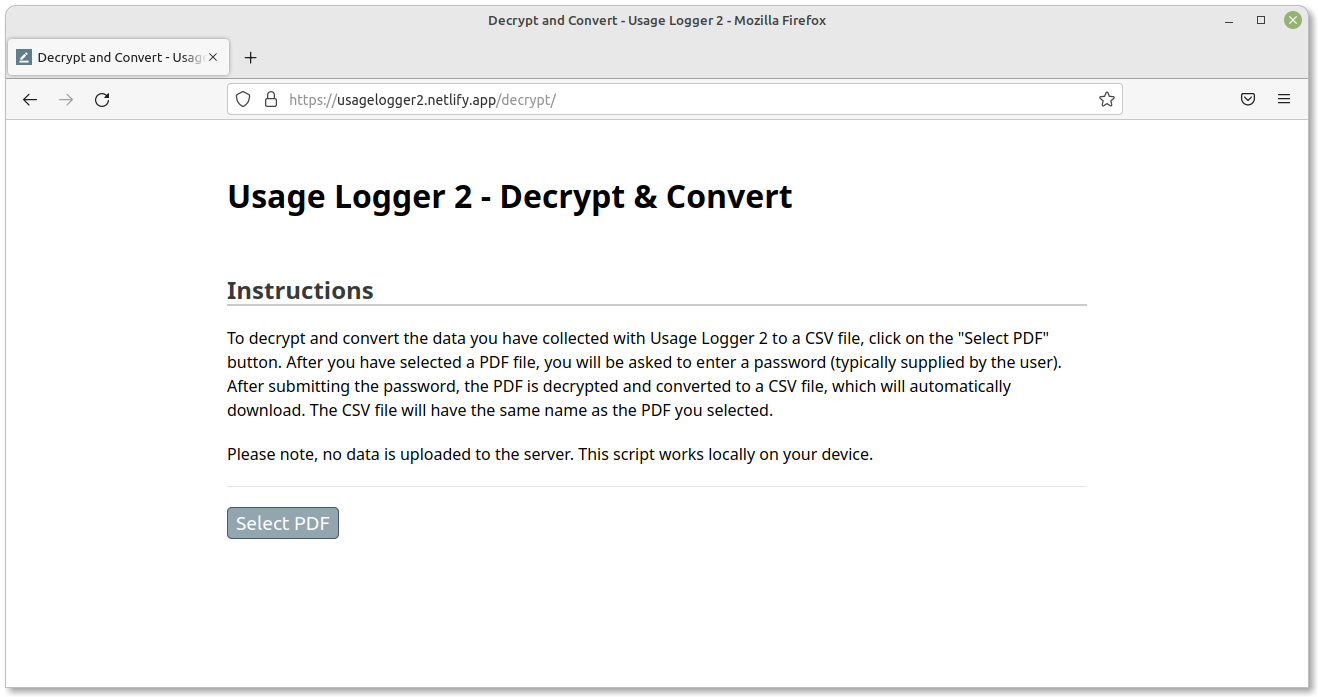
This website handles the decryption process specifically for the output of the Usage Logger.
To decrypt the Usage Logger data, simply click on the 'Select PDF' button. Once you have selected a PDF file from your computer, you will be prompted to insert a password. Upon entering the correct password, the PDF is automatically converted to a CSV file and downloaded to your standard browser download folder.
Analysis
The analysis can be carried out in python and R. For Python, there are Jupyter Notebooks available in the Github repository. These can be used to analyse:
A number of R scripts are also provided.
Contact
In case of problems or questions, please contact Dr. Heather Shaw at h.shaw5@lancaster.ac.uk.